
Rarely in the infosec industry do cyber investigators get the luxury of knowing the full scope of their adversary’s campaign — from tasking to actual operations, all the way to completion. The oft-repeated mantra “attribution is hard” largely stands true. Short of kicking down the door just as a cyber actor pushes enter, it is frustratingly hard to prove who is responsible for cyberattacks with 100 percent certainty. However, a series of recent U.S. Department of Justice (DoJ) indictments released over the course of two years, combined with CrowdStrike® Intelligence’s own research, offers startling visibility into a facet of China’s shadowy intelligence apparatus.

Figure 1. Leap Engine
This is Part I of a three-part blog series that will take a look at how Beijing used a mixture of cyber actors – sourced from China’s underground hacking scene, Ministry of State Security (MSS/国安部) officers, company insiders, and state directives – to fill key technology and intelligence gaps in a bid to bolster production of dual-use turbine engines. Such engines could be used for both energy generation and to enable its narrow-body twinjet airliner, the C919, to compete against western aerospace firms.
What follows is a remarkable tale of traditional espionage, cyber intrusions, and cover-ups, all of which overlap with activity CrowdStrike Intelligence has previously attributed to the China-based adversary TURBINE PANDA. These operations are ultimately traceable back to the MSS Jiangsu Bureau, the likely perpetrators of the infamous 2015 U.S. Office of Personnel Management (OPM) breach.
Part I focuses on the target of this complex and sophisticated cyberattack.
The Target
The story starts with a simple fact: Beijing accurately predicted that due to its rising economic status, China’s middle-class demand for air travel would far outpace its ability to supply aircraft and a domestic commercial aviation industry capable of supporting these logistics. Putting aside the obvious military-civil (军民融合) benefits that turbine engines have for the energy and aviation sectors, much of China’s strategic push into this industry is predicated on necessity. China is predicted to succeed the U.S. as the world’s largest aviation market by 2022, adding nearly one billion passengers by 2036. From China’s 12th and 13th Five Year Plans to the increasingly scrutinized Made in China 2025 Plan, numerous state strategic plans have named aerospace and aviation equipment as one of ten priority industries to focus on “leap-frog” developments.
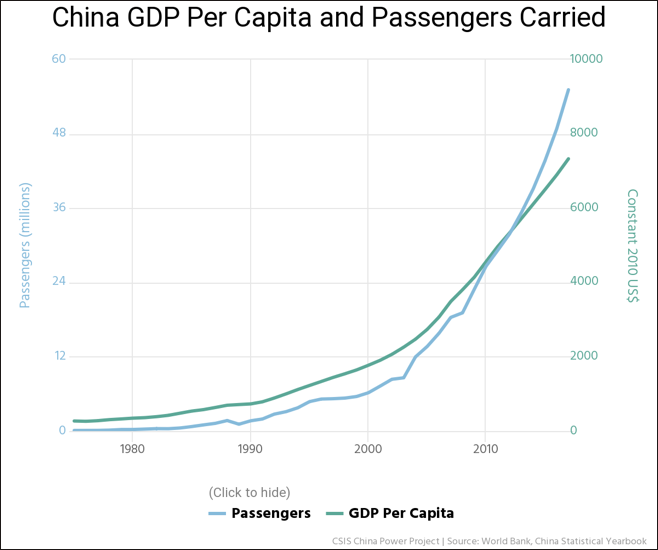
Figure 2. China’s Exponential Growth in Air Travel Mirrored by Rise of China’s
Middle Class
Obstacles to Chinese-Built Commercial Aircraft
A major focus of this strategy centered on developing an indigenous Chinese-built commercial aircraft designed to compete with the duopoly of Western aerospace. That aircraft would become the C919 — a plane roughly half the cost of its competitors, which completed its maiden flight in 2017, after years of delays due to design flaws.
However, the C919 can hardly be seen as a complete domestic triumph, because it is reliant on a plethora of foreign-manufactured components. Likely in an effort to bridge those gaps, the Chinese state-aligned adversary TURBINE PANDA conducted cyber intrusions from roughly 2010 to 2015 against several of the companies that make the C919’s various components.
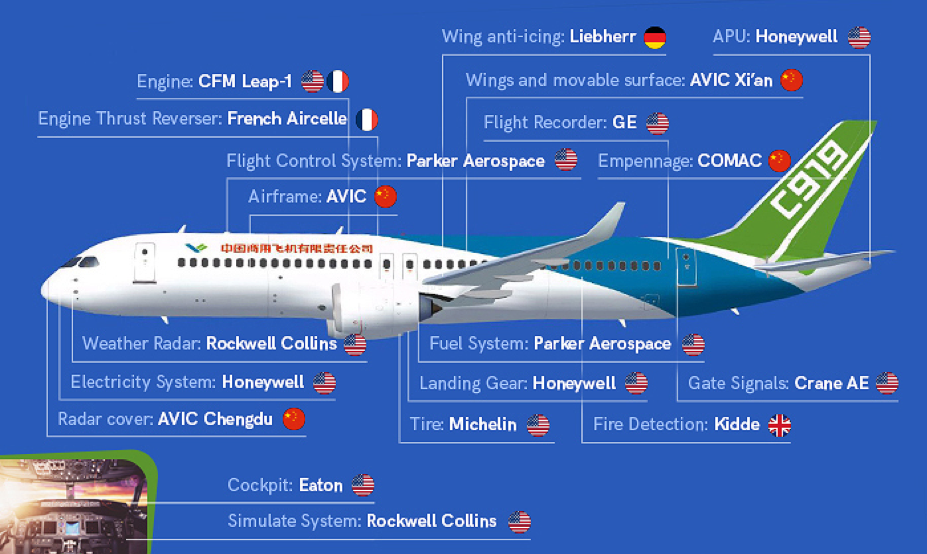
Figure 3. Components of C919
Specifically, in December 2009, the state-owned enterprise (SOE) Commercial Aircraft Corporation of China (COMAC/中国商用飞机有限责任公司) announced it had chosen CFM International’s LEAP-X engine (a joint venture between U.S.-based GE Aviation and French aerospace firm Safran, formerly Snecma) to provide a custom variant, the LEAP-1C engine, for the newly announced C919.
The deal was reportedly signed in Beijing during a visit by then-French Prime Minister François Fillon. Despite the early deal with CFM, both COMAC and fellow SOE, the Aviation Industry Corporation of China (AVIC/中国航空工业集团公司), were believed to be tasked by China’s State-owned Assets Supervision and Administration Commission of the State Council (SASAC) with building an “indigenously created” turbofan engine that was comparable to the LEAP-X.
A Dramatic Reduction in Dev Time
In August 2016, both COMAC and AVIC became the main shareholders of the Aero Engine Corporation of China (AECC/中国航空发动机集团), which produced the CJ-1000AX engine. The CJ-1000AX bears multiple similarities to the LEAP-1C, including its dimensions and turbofan blade design. The AECC conducted its first test as recently as May 2018, having overcome significant difficulties in their first mockups.
Though it is difficult to assess that the CJ-1000AX is a exact copy of the LEAP-X without direct access to technical engineering specifications, it is highly likely that its makers benefited significantly from the cyber espionage efforts of the MSS, which will be detailed further in subsequent blog installments, knocking several years (and potentially billions of dollars) off its development time.
Multifaceted, Targeted Attacks
The actual process by which the CCP and its SOEs provide China’s intelligence services with key technology gaps for collection is relatively opaque, but what is known from CrowdStrike Intelligence reporting and corroborating U.S. government reporting is that Beijing uses a multifaceted system of forced technology transfer, joint ventures, physical theft of intellectual property from insiders, and cyber-enabled espionage to acquire the information it needs.
Specifically, SOEs are believed to help identify major intelligence gaps in key projects, which China’s intelligence services then are likely tasked with collecting. It is assessed with high confidence that the MSS was ultimately tasked with targeting firms that had technologies pertaining to the LEAP-X engine and other components of the C919, based on timing and the details revealed in the DoJ indictments.
For example, the first preparatory activity in January 2010, believed to be associated with TURBINE PANDA, targeted Los Angeles-based Capstone Turbine and began just a month after choosing CFM as its engine provider.
This brings us to our culprits: the Jiangsu Bureau of the MSS (JSSD/江苏省国家安全厅) located in Nanjing. In Part II, we will discuss the JSSD’s location, and the joint operations between JSSD’s cyber operators and its human intelligence officers.
Additional Resources
- Download the entire report: “Huge Fan of Your Work: How TURBINE PANDA and China’s Top Spies Enabled Beijing to Cut Corners on the C919 Passenger Jet.”
- Read the 2019 Global Threat Report: “Adversary Tradecraft and the Importance of Speed.”
- Read the 2019 Falcon OverWatch Report: “Observations From the Front Lines of Threat Hunting.”
- Learn more about the CrowdStrike Falcon® Platform by visiting product webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent
 today.
today.
The post Huge Fan of Your Work: How TURBINE PANDA and China’s Top Spies Enabled Beijing to Cut Corners on the C919 Passenger Jet — Part I appeared first on .
Go to Source
Author: Adam Kozy


