PCI DSS applies to merchants and other entities that store, process, and/or transmit cardholder data.
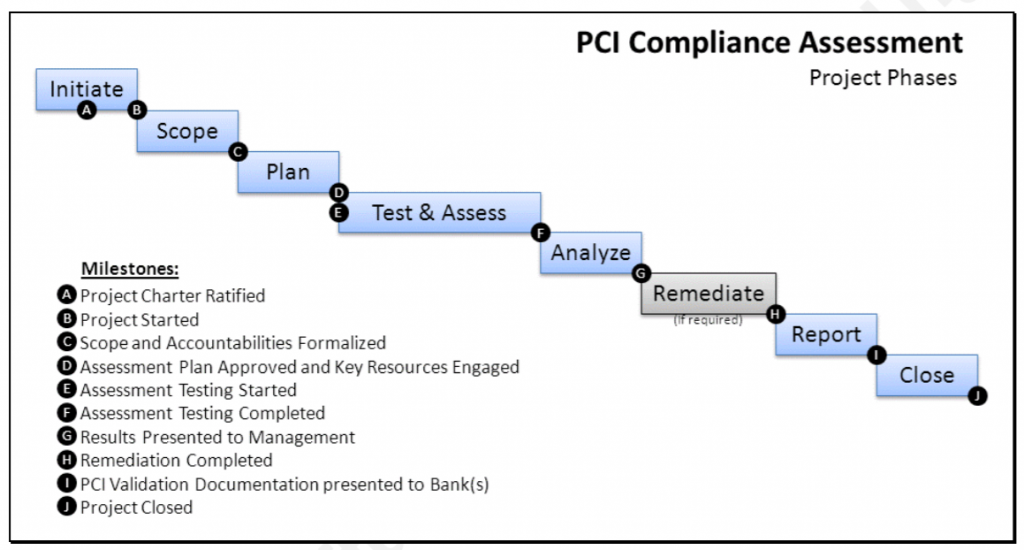
- Scope – determine which system components and networks are in scope for PCI DSS
- Assess – examine the compliance of system components in scope following the testing procedures for each PCI DSS requirement
- Report – assessor and/or entity completes required documentation (e.g. Self-Assessment Questionnaire (SAQ) or Report on Compliance (ROC)), including documentation of all compensating controls
- Attest – complete the appropriate Attestation of Compliance (AOC)
- Submit – submit the SAQ, ROC, AOC and other requested supporting documentation such as ASV scan reports to the acquirer (for merchants) or to the payment brand/requestor (for service providers)
- Remediate – if required, perform remediation to address requirements that are not in place, and provide an updated report
Choosing a Qualified Security Assessor (QSA)
A Qualified Security Assessor (QSA) is a data security firm that is qualified by the PCI Security Standards Council to perform on-site PCI DSS assessments. The QSA will:
- Verify all technical information given by merchant or service provider
- Use independent judgment to confirm the standard has been met
- Produce the final report
Choosing an Approved Scanning Vendor (ASV)
An Approved Scanning Vendor (ASV) is a data security Qualified by PCI council firm using a scanning solution to determine whether or not the customer meets the PCI DSS external vulnerability scanning requirement.
- An ASV may use its own software or an approved commercial or open source solution.
- Tests not permitted by the ASV solution include denial of service, buffer overflow, brute force attack resulting in a password lockout, or excessive usage of available communication bandwidth.
- An ASV scanning solution includes the scanning procedures and tool(s), the associated scanning report.
Scope of PCI DSS Requirements
- The scoping process includes identifying all system components that are located within or connected to the cardholder data environment.
- Scoping must occur at least annually and prior to the annual assessment.
- The cardholder data environment is comprised of people, processes, and technology that handle cardholder data or sensitive authentication data.
- System components include network devices (both wired and wireless), servers, computing devices, and applications.
- Virtualization components, such as virtual machines, virtual switches/routers, virtual appliances, virtual applications/desktops, and hypervisors, are also considered system components within PCI DSS.
Network Segmentation
- Scope can be reduced with the use of segmentation, which isolates the cardholder data environment from the remainder of an entity’s network
- To be considered out of scope for PCI DSS, a system component must be properly isolated (segmented) from the CDE, such that even if the out-of-scope system component was compromised it could not impact the security of the CDE
Reporting (SAQ, AOC, ROC)
Depending on payment card brand requirements, merchants and service providers may need to submit an SAQ for self-assessments, or a ROC Report on Compliance for on-site assessments.
Quarterly submission of a report for network scanning may also be required.
Using the Self-Assessment Questionnaire (SAQ)
The “SAQ” is a validation tool for merchants and service providers to report the results of their PCI DSS self-assessment, if they are not required to submit a Report on Compliance (ROC).
The Questionnaire includes a series of yes-or-no questions for each applicable PCI Data Security Standard requirement. If an answer is no, your organization may be required to state the future remediation date and associated actions.
An Attestation of Compliance (AOC).
- An Attestation of Compliance is that you are eligible to perform and have performed the appropriate Self-Assessment.
- The AOC is a form used by merchants and service providers to attest to the results of a PCI DSS assessment.
- It is submitted to an acquirer or payment brand along with the appropriate SAQ or ROC, plus any other requested documentation.
- The QSA completes an Attestation of Compliance (AOC) that is sent to the retailer’s merchant bank who then sends it to the appropriate card brand
Information Contained in PCI DSS Report on Compliance (ROC)
A Report on Compliance (ROC) tests the standards that are in place to protect the credit card information.
- A PCI ROC is required for all Level 1 Merchants. A Level 1 Merchant is a retailer that has more than 6 million annual transactions with Visa and/or Mastercard.
- A ROC must be completed by a Qualified Security Assessor (QSA) after an audit, and subsequently submitted to the merchant’s acquirer.
- The acquirer, after accepting the ROC, sends it to the payment brand for verification.
Documents required at different levels:
- Level 1 Merchant – ROC & Quarterly External ASV Scans
- Level 2 Merchant – ROC or appropriate SAQ & Quarterly External ASV Scans (depending on card brand requirements)
- Level 3 Merchant – Appropriate SAQ & Quarterly External ASV Scans
Report on Compliance (ROC )includes
- Contact Information and Report Date
- Executive Summary
- Description of entity’s payment card business
- high level network diagram
- Description of Scope of Work and Approach Taken
- Description of how the assessment was made
- Environment, Network segmentation used,
- Details for each sample set selected and tested
- Wholly owned or international entities requiring compliance with PCI DSS, wireless networks or applications that could impact security of cardholder data
- Version of PCI DSS used to conduct the assessment)
- Details about Reviewed Environment
- Diagram of each network
- Description of cardholder data environment
- List of all hardware and software in the CDE
- Service providers used
- Third party payment applications, individuals interviewed
- Documentation reviewed
- Details for reviews of managed service providers)
- Quarterly Scan Results
- summary of four most recent ASV scan results
- Findings and Observations
- Detailed findings on each requirement and sub-requirement
- Explanations of all N/A responses
- validation of all compensating controls.



